The Ultimate GRC Training Become a GRC Expert!
Complete Training by Cyvitrix Learning
Start Now
START YOUR CAREER IN GRC
What makes our GRC course a great fit?
- Dive deep into essential GRC concepts, including governance frameworks, risk management strategies, compliance standards, and regulatory requirements.
- Learn from industry experts with extensive GRC experience and gain insights into best practices and real-world scenarios.
- Collaborate with fellow learners and instructors, participate in meaningful discussions, and have your questions answered by experts in the field.
Based on Market research and survey information, salary ranges for different GRC positions can be as follows in the US & Global Market!
- GRC Analyst/Associate: The salary for entry-level GRC positions typically ranges from $50,000 to $80,000 per year, depending on location and industry.
- GRC Consultant/Advisor: Mid-level GRC professionals with a few years of experience can expect salaries ranging from $80,000 to $120,000 annually. Again, this can vary based on location and industry specialization.
- GRC Manager/Senior Consultant: As professionals progress in their careers and take on managerial or senior consultant roles, salaries can range from $100,000 to $150,000 per year, depending on experience, industry, and the organization's size.

Start Now
GRC - Governance, Risk & Compliance
GRC Complete Training
Governance, Risk & Compliance
GRC Bootcamp Training - Self Based
IT & Cyber Security Auditing
IT Auditing Complete Course
Information Technology Auditing
IT Audit Bootcamp Training - Self Based
LEARNERS' reviews
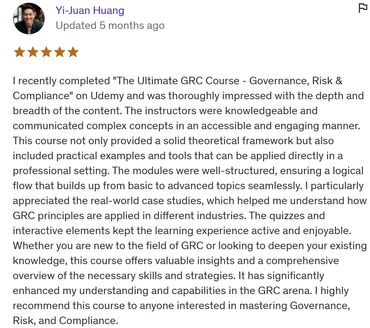
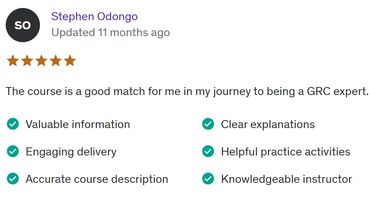
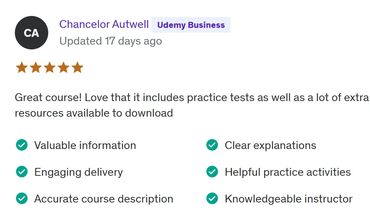

Course introduction
Know more about our Ultimate GRC Training.
Start Now
Course Content
Introduction to Cybersecurity & Information Security
- Key Security Terminologies 🔑: Understanding basic terms used in cybersecurity.
- Malware 🦠: Types of malwares and their impact.
- Cybersecurity Attacks ⚔️: Common forms of cyber-attacks.
- Web Application Attacks 🌐: Specific threats targeting web applications.
Security Program and Governance
- Purpose of the Security Program 🎯: How organizations use security programs to protect data.
- Cybersecurity vs. Information Security & Information Assurance 🔐: Differences between these concepts.
- Security Goals and Strategy 🛡️: Defining objectives for maintaining a secure environment.
- Security Roles and Responsibilities 👥: Understanding the roles of security managers and other key positions.
- Information Security Standards and Frameworks 📋: Overview of standards like ISO 27001 and NIST.
- Laws, Regulations, and Privacy Requirements ⚖️: Legal implications affecting security.
- Gap Analysis 🔍: Identifying weaknesses in security practices.
- Acquiring New Technology 🖥️: Steps in implementing new technologies with security in mind.
- Feasibility Analysis and Business Case 💡: Justifying technology investments.
Risk Management
- Overview and Key Terminologies 📊: Basics of risk management in cybersecurity.
- Risk Identification, Analysis, Reporting, and Monitoring 📈: Processes for managing and reducing risks.
- Key Risk Indicators (KRIs) 🚨: Metrics used to monitor risk.
- Risk Frameworks 🧩: Understanding various risk management frameworks.
- Threat Modeling 🎯: Identifying potential threats.
- Vendor and Supply Chain Risk Management 🏗️: Ensuring security in third-party relationships.
- SOC Reports & Outsourcing 📄: Importance of service organization control reports in risk management.
Security Policies and Procedures
- Personnel Security and Awareness Programs 👤: Measures for securing personnel and educating them on security.
- Policies and Procedures 📜: Developing and reviewing key policies like Acceptable Use Policy (AUP) and Clear Desk.
- Security Controls 🛡️: Implementation and assessment of controls for defense.
- Defense in Depth 🏰: Layered security approach.
Auditing and Compliance
- Information System Auditing 📑: Planning and executing security audits.
- Audit Committees 🏛️: Their role in overseeing audit processes.
- Audit Execution & Evidence Collection 🕵️: How audits are performed and evidence is gathered.
- Control Evaluation & Audit Reporting 📝: Analyzing controls and documenting audit findings.
Network, Endpoint, and Data Security
- IT Infrastructure and Network Topology 🖧: Overview of network designs and their security implications.
- Wireless, VoIP, IoT Security 📡: Securing different types of devices and networks.
- Endpoint Security 💻: Protecting devices with Endpoint Protection Platforms (EPP).
- Active Directory & LDAP 🔑: Overview of directory services for managing user access.
- Data Security 🛢️: Methods for protecting and destroying data, data classification, and compliance with retention policies.
- Database Security 🗄️: Securing database systems and access control models.
Physical Security
- Physical Security Best Practices 🏢: Protecting physical assets from threats.
Incident Management and Business Continuity
- Incident Response 🚨: Steps in managing security incidents.
- Disaster Recovery and Business Continuity Planning (BCP/DRP) 🌪️: Planning for and recovering from disasters.
- RTO and RPO ⏳: Key metrics in disaster recovery.
Software Development Process
- Development Methodologies 🖥️: Best practices in secure coding and software development (DevOps, DevSecOps).
- Release Management & Software Licensing 🔑: Managing software updates and licensing issues.
IT Management
- Asset and Change Management 🗃️: Keeping track of IT assets and managing changes.
- Penetration Testing and Vulnerability Assessments 🛠️: Methods for testing and securing systems.
- Patch Management 🔄: Keeping systems up to date with security patches.
Start Now
Who this course is for?
- IT managers who are responsible for managing IT operations and ensuring they are aligned with business objectives and comply with legal and regulatory requirements.
- IT professionals responsible for implementing and managing IT processes, such as IT service management, IT security, and IT risk management.
- Compliance professionals who are responsible for ensuring that the organization's IT processes comply with legal and regulatory requirements.
- They are responsible for identifying and managing IT risks.
- Governance, Risk, and Compliance Professionals
WHY TO JOIN OUR COURSES?
Our dedicated instructor is committed to delivering the best learning experience possible. They are actively available to address any questions or concerns you may have during the course. Additionally, they regularly review and update the course content to ensure its relevance and effectiveness.
Upon successfully completing this course, you will receive a certificate of completion from the renowned Udemy platform. This certificate can serve as a valuable addition to your CV/Resume, demonstrating your dedication to professional development and showcasing your accomplishment in completing the course.
You can rest assured that your learning journey is supported by an instructor who is invested in your success. Their presence and responsiveness provide you with the guidance and assistance needed to maximize your understanding and make the most of the course materials.
WHAT DO THEY SAY ABOUT US?
Start Now
Whether you're looking to advance your career, start a new one, or enhance your understanding of cybersecurity, Cyvitrix is your trusted partner. With our courses, you're investing not just in education but in your future.
Take the first step towards empowering your digital life. Enroll in a Cyvitrix course today.
Sign up to hear from us about specials, sales, and events.




















